Last month, we announced the winner of the Fall semester Watch_Dogs® 2 CTF challenge and taught you how to solve Level 1 of the CTF, Miss Marple.
If you haven’t yet had a chance to try out the challenges, you can still head over to https://watchdogs.mlh.io/ and log in with MyMLH to give it a shot before reading the spoilers below.
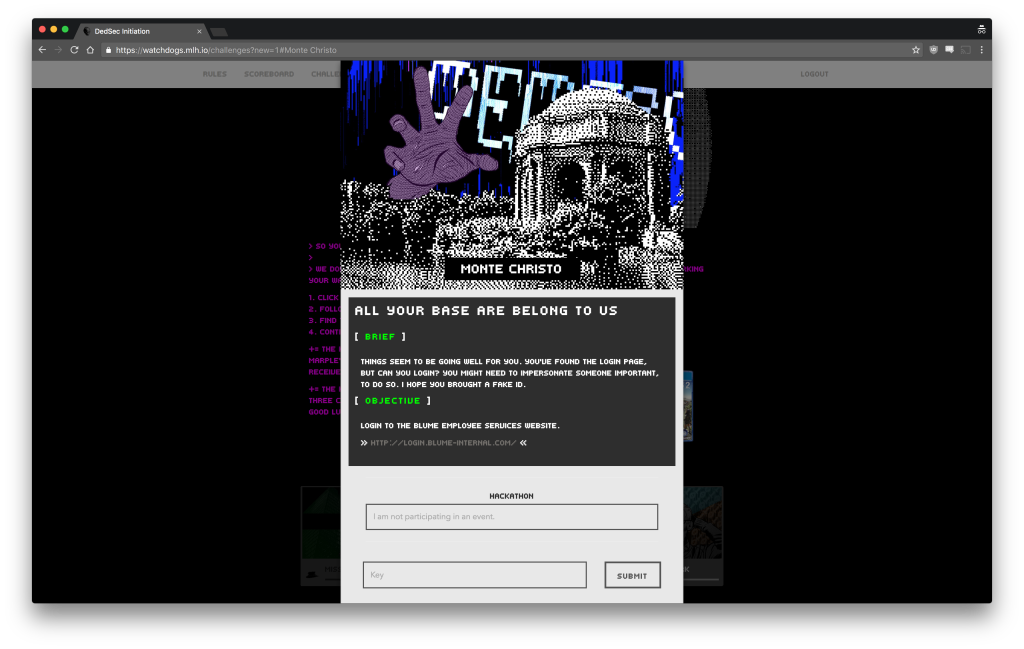
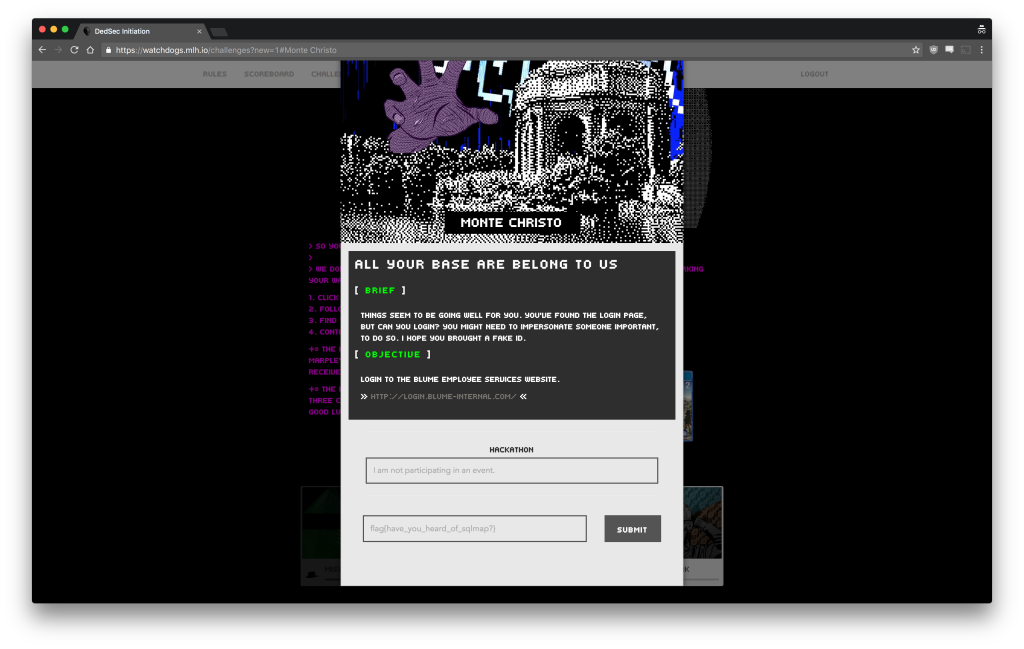
In this post we’re going to teach you how to solve CTF Level 2, Monte Christo.
Level 2: Monte Christo
The second level of the CTF utilizes a SQL injection to gain entry to a secure page.
To start things off, you are told that you may need to impersonate someone on the login portal.
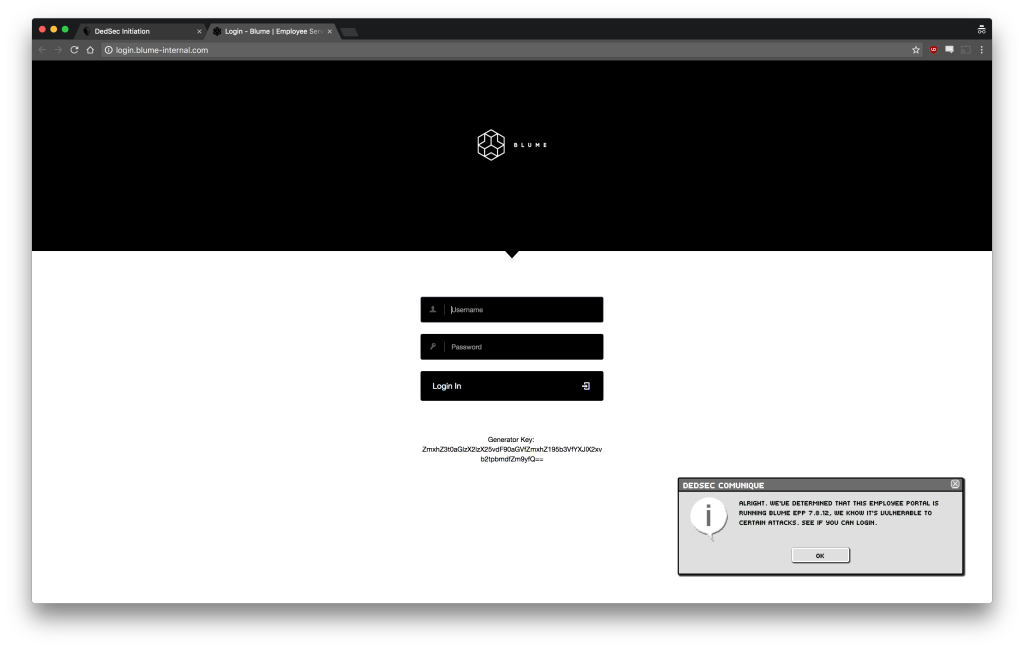
Once you click through, you are given a hint that the login portal is vulnerable to certain attacks. This is the time where you should test obvious vulnerabilities that a login system might typically have.
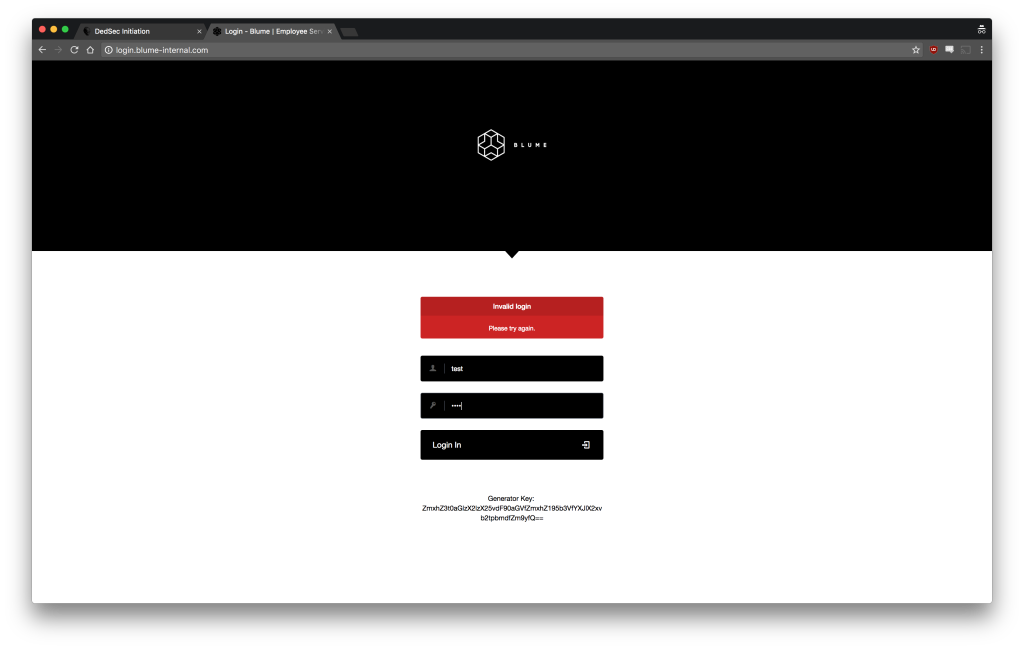
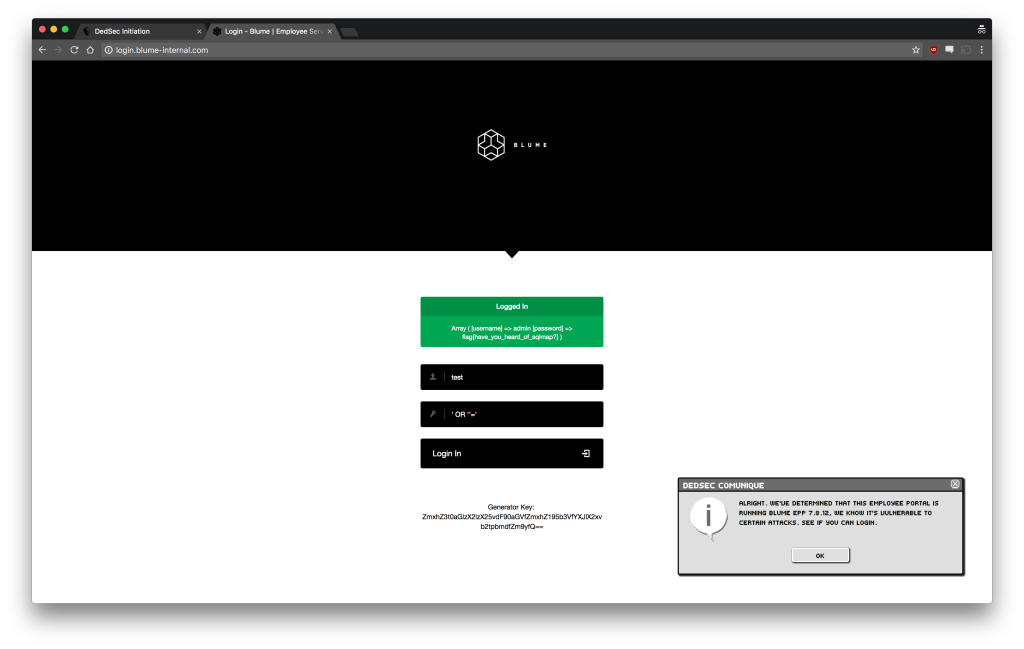
The first and most obvious thing to do is to try some basic login combinations that might exist by default in a user database. But if you type in test as both the username and password, it simply refuses your entry. This is expected behavior for any login system.
Once we’ve determined that default username and password combinations won’t work, we should try some alternate vulnerabilities. At this point, it is important to understand some things about SQL, which we mentioned at the beginning of this post.
SQL is a language that is used to communicate with relational databases like PostgreSQL or MySQL. A simple SQL command might look like the following:
SELECT name FROM users;
INSERT INTO users SET name=’Jon’;
If you want to learn more about SQL and how to write commands, you can read some of the tutorials from SQLZOO.
When writing software to interact with SQL databases, a developer might write the queries themselves and use a function to send those queries to the database for execution. Alternatively, they might use a library that generates the text queries for them based on functions they call.
A SQL injection vulnerability, which we told you above was the solution to Level 2, is when a malicious user writes their own SQL query into a user-facing field that gets executed against the database.
Developers allow this basic vulnerability to occur surprisingly frequently by not sanitizing, filtering out or escaping user inputs before making them part of queries that are executed on the database. You can learn some strategies to protect against SQL injections here.
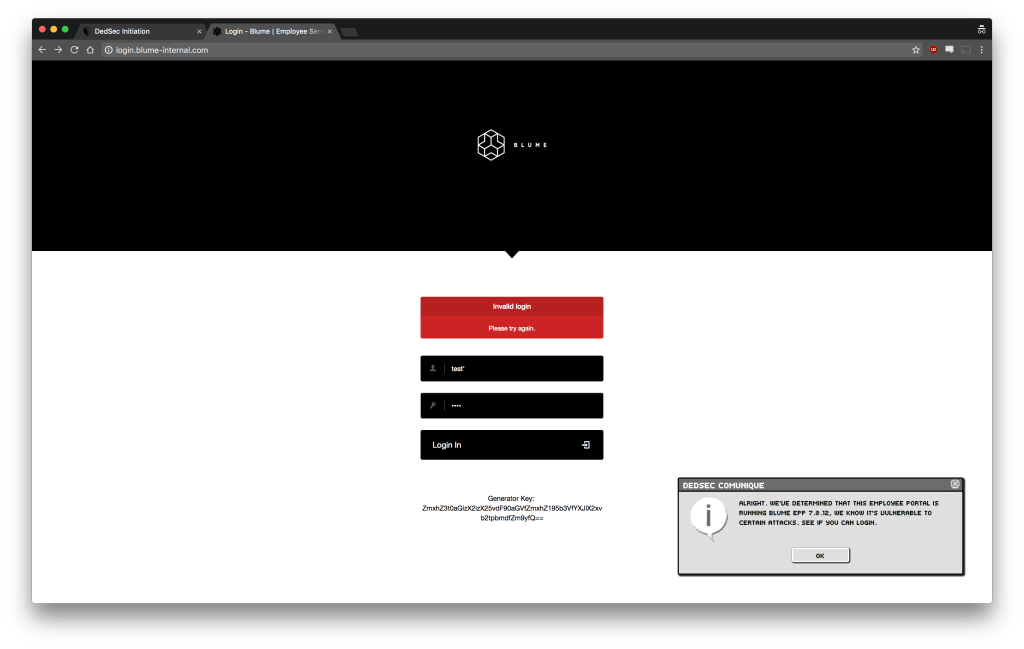
To test if an application is vulnerable to SQL injections, you might try putting characters in an input field that would typically break a query. For example if you add a single quote (‘) to the username field, you can see that we get a MySQL error in response.
By performing that simple test, you discovered that the developer is directly passing whatever is in the username or password field into the database. Now you can use that to your advantage to break into the database.
You’ll want to modify the SQL query that the developer is submitting to the database to return a TRUE value no matter what so that the system thinks that you have a valid username and password.
You can assume that the query to check for a valid login looks something like this:
SELECT * FROM users WHERE username=’$USERNAME’ AND password=’$PASSWORD’;
If you want this to always return a valid user entry, you’ll need to make sure the WHERE condition always returns TRUE, so you can put my SQL injection into one of the fields and submit it.
Based on what you put in the password field above, the SQL query that gets submitted to the database actually looks like this:
SELECT * FROM users WHERE username=’test’ AND password=” OR ”=”;
No matter what the username and password are, my OR condition will always be TRUE. This lets the database return whatever the first user entry is. Lucky for me, the flag is returned since my login was deemed successful.
You can now go submit it back on the CTF page.
You might assume that SQL injections are easy to protect against, but many developers forget to implement basic user input filtering and leave themselves vulnerable to malicious users. There is even a SQL Injection Hall of Shame and a famous XKCD comic that tackle this simple attack:
I hope you enjoyed our CTF Level 2 tutorial, stay tuned for Level 3 coming soon and be sure to try Watch_Dogs® 2 on your preferred gaming platform!